Three of the most recent major critical infrastructure attacks in 2021 have taken advantage of gaping security vulnerabilities in the nation’s crucial water, gas and food supplies.
In early February, a Florida water treatment plant in Oldsmar, a small city just west of Tampa, had its computer system breached. The result was levels of sodium hydroxide were raised to more than 1,000 times the acceptable levels. This chemical, the same ingredient used in drain clear, skyrocketed the toxicity of the city water could have potentially sickened thousands of residents if the attack had not been detected.
Then on May 10, the largest attack against U.S. critical infrastructure occurred when Colonial Pipeline, the nation’s largest fuel pipeline, was forced to shut down operations when faced with a ransomware attack. For almost two weeks, gas stations up and down the U.S. East Coast and as far west as Texas were either out of gas completely or rationing what they had. More than a month following the attack, gas prices remain high as a result.
And in June, JBS, the largest meat processer in the U.S., supplying up to a fifth of the nation’s meat supply, was forced to cease operations due to a cyberattack. JBS was just one of the latest major food and beverage companies that have been victimized over the last decade.
With the Global Critical Infrastructure Protection (CIP) market expected to grow from an estimated $92 billion in 2018 to more than $118 billion by 2028, security professionals realize the imminent threat this sector is under and have committed to tightening security in both cyber and physical security environments. The report states that the majority of CIP programs that have been initiated or revised in recent years focus on adopting a risk management approach. This focus has the CIP sector continuously engaged in identifying major security assets, analyzing risks and formulating strategies to best prioritize mitigating risks.
Perhaps the biggest challenge to protecting the nation’s critical infrastructure is the fact that more than 80% are owned by the private sector. This creates substantial friction when expensive security and risk mitigation programs are constrained by tight institutional economic realities and a lack of proper oversight.
How then, can the critical infrastructure sector ensure that it can protect itself and the nation from catastrophic physical and cyber chaos? It is key that a strong critical infrastructure security and resilience program be based on collaboration and information sharing. Collaboration can be facilitated by establishing processes necessary for government(s) and the private sector to communicate freely without releasing proprietary information or providing an unfair advantage. A trusted information-sharing environment will allow stakeholders to share crucial data that can strengthen security and resilience.
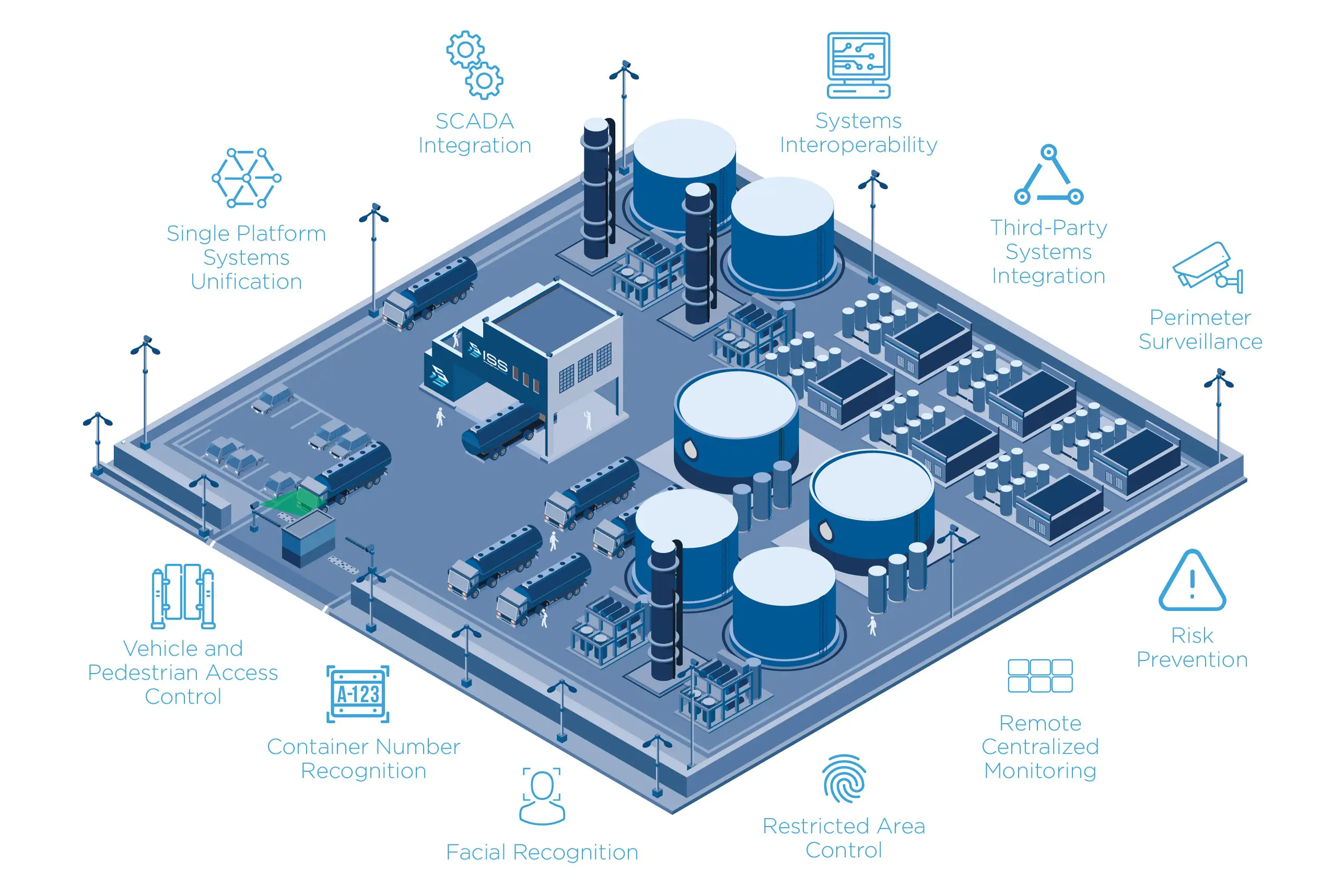
Advanced technology solutions can facilitate collaborative and resilient security programs when used in tandem within a strong risk and compliance framework. It is this approach that Intelligent Security Systems (ISS) employs to construct comprehensive digital video surveillance and control systems solutions that are cutting edge and tailored to each project. This is most important for critical infrastructure since it allows for solutions that are open, flexible and scalable and permits centralized command and control of an entire enterprise security network in a single place.
The integrated platform that typifies the ISS solutions includes video management (VMS), license plate recognition (ANPR/LPR), facial recognition, container number recognition, and Under Vehicle Surveillance (UVSS) that can all be deployed in tandem to form a security blanket around critical infrastructure sites. Video surveillance systems, using advanced analytics built on Intel Artificial Neural Network technology, can monitor both security and safety issues and alert staff when problems arise. At the industrial level, surveillance can also be used to monitor productivity. ISS can also integrate an array of security solutions from full Building Management Systems and life safety to access control.
Solutions That Work for Critical Infrastructure
 SecurOS® VMS: A robust video management system that incorporates native video analytics is a key element of securing a critical infrastructure site. The advantage of this option is it can be tailored to almost any sized application but is especially useful at the enterprise level. The ISS SecurOS® platform is an end-to-end solution that integrates with most third-party security systems including access control, fire/life safety and building management. For large and complex security requirements, the SecurOS® Enterprise can manage and monitor an unlimited number of cameras and devices, apply intelligent video analytics, and act as an integration platform for a variety of third-party systems.
SecurOS® VMS: A robust video management system that incorporates native video analytics is a key element of securing a critical infrastructure site. The advantage of this option is it can be tailored to almost any sized application but is especially useful at the enterprise level. The ISS SecurOS® platform is an end-to-end solution that integrates with most third-party security systems including access control, fire/life safety and building management. For large and complex security requirements, the SecurOS® Enterprise can manage and monitor an unlimited number of cameras and devices, apply intelligent video analytics, and act as an integration platform for a variety of third-party systems.
Some of the basic functionality of the SecurOS® Enterprise platform includes:
- Robust architecture that can manage an infinite number of cameras, servers, access control devices and analytic modules.
- Sophisticated, built-in analytics package that enables license plate, facial and container number recognition, along with object tracking, unattended object detection and people counting.
- Dynamic hardware/software solutionsthat along with an LPR camera kit, includes a speeding violation camera kit, intersection violations solution and an under-vehicle surveillance system.
- An open architecture platform allows the Enterprise VMS to address seamless device integration with third-party vendors to provide a single pane of glass when it comes to monitoring real-time events.
 SecurOS® Auto License Plate Recognition (LPR/ANPR): This solution is a dynamic data-collection resource that can accurately capture license plate information at 155 mph and in all kinds of weather conditions, including fog, rain and snow. The advanced deep learning and template-based algorithms work with pinpoint accuracy to help distinguish letters from numbers, like deciphering the number 8 from the letter B. In addition, the solution easily integrates with third-party parking management or smart roadway systems and any legacy security equipment or external databases.
SecurOS® Auto License Plate Recognition (LPR/ANPR): This solution is a dynamic data-collection resource that can accurately capture license plate information at 155 mph and in all kinds of weather conditions, including fog, rain and snow. The advanced deep learning and template-based algorithms work with pinpoint accuracy to help distinguish letters from numbers, like deciphering the number 8 from the letter B. In addition, the solution easily integrates with third-party parking management or smart roadway systems and any legacy security equipment or external databases.
Other key features include the ability to determine the average speed and direction of vehicles captured on the scene and identify their origin to the captured license plate. The solution will also indicate the place, time and date of the captured plate.
 Under Vehicle Security Systems (UVSS): This unique technology has emerged as a key risk mitigation element for security professionals who understand that the undercarriage of a vehicle is an important threat vector. The ISS system creates a database of high-resolution undercarriage images and recognized vehicle license plates, making it ideal for numerous venues where underground parking or structured parking facilities are utilized.
Under Vehicle Security Systems (UVSS): This unique technology has emerged as a key risk mitigation element for security professionals who understand that the undercarriage of a vehicle is an important threat vector. The ISS system creates a database of high-resolution undercarriage images and recognized vehicle license plates, making it ideal for numerous venues where underground parking or structured parking facilities are utilized.
 SecurOS® Cargo: With a growing threat of supply chain disruption, the ISS solution for cargo container number recognition is a popular piece of critical infrastructure risk planning. The video analytic module recognizes the ISO codes from cargo containers at port entrance. The system then captures the codes that are printed either horizontally or vertically from above, back of either side of the container and can consolidate all data assigned to that container into one result from the camera. Because the module integrates with cargo management processes at ports, intermodal and logistics center, the system rapid calculus of information reduces liability and improves the accuracy of identifying containers at large facilities.
SecurOS® Cargo: With a growing threat of supply chain disruption, the ISS solution for cargo container number recognition is a popular piece of critical infrastructure risk planning. The video analytic module recognizes the ISO codes from cargo containers at port entrance. The system then captures the codes that are printed either horizontally or vertically from above, back of either side of the container and can consolidate all data assigned to that container into one result from the camera. Because the module integrates with cargo management processes at ports, intermodal and logistics center, the system rapid calculus of information reduces liability and improves the accuracy of identifying containers at large facilities.
 SecurOS FaceX Capture and Facial Recognition: There is no denying the importance this biometric plays in a comprehensive security plan. The ISS solution operates in a wide range of conditions, such as changing illumination and angle and is capable of unlimited database sizes. Again, integration is a selling point with FaceX since it is a seamless blend of video and access control. It allows a subject’s face to act as their credential, providing touchless and hands-free interactions. A prime security feature is the anti-spoofing technology that monitors facial accuracy and liveness against printed ID photos or digital mobile devices.
SecurOS FaceX Capture and Facial Recognition: There is no denying the importance this biometric plays in a comprehensive security plan. The ISS solution operates in a wide range of conditions, such as changing illumination and angle and is capable of unlimited database sizes. Again, integration is a selling point with FaceX since it is a seamless blend of video and access control. It allows a subject’s face to act as their credential, providing touchless and hands-free interactions. A prime security feature is the anti-spoofing technology that monitors facial accuracy and liveness against printed ID photos or digital mobile devices.
Conclusion
Critical infrastructure is a foundational aspect of societal and economic preservation. Any disruption to the systems that provide the nation its energy, food, water, pharmaceutical, emergency services, health and public safety, transportation and government infrastructure can substantially impact our lives. Combining technology with a proactive risk mitigation approach can ensure critical infrastructure security and resilience today and in the future.
We look forward to hearing from you. Just click here to contact us today